.png.6853eaf0f6da03aa3fe5b1c6bd5167a4.png)
Everything posted by cambaz
-
Themida/Winlicense unpacker (Unlicense)
Themida 3.x - 2x unpacker ımport fixer unlincense 32&64 bit A Python 3 tool to dynamically unpack executables protected with Themida/WinLicense 2.x and 3.x. Warning: This tool will execute the target executable. Make sure to use this tool in a VM if you're unsure about what the target executable does. Note: You need to use a 32-bit Python interpreter to dump 32-bit executables. Feautures; Handles Themida/Winlicense 2.x and 3.x Handles 32-bit and 64-bit PEs (EXEs and DLLs) Handles 32-bit and 64-bit .NET assemblies (EXEs only) Recovers the original entry point (OEP) automatically Recovers the (obfuscated) import table automatically link.txt
-
SNOWMAN Plugin for debuggers [GIT-HUB]
What is Snowman? - Snowman is Native Code to C/C++ decompiler. - U can easily get ur C++ or C code to a Sudo (Native Code). - Then u can find the functions by your-self easily. Supports x86 Applications, AMD64, ARM architectures. Note U can use it with IDA, x64dbg, radare2, ollydbg, gHidra, or standalone software. link.txt
-
🔧 C++ Enigma Protector 5.x–7.x Dumper & PE Fixer Tool [Dump + Auto IAT + EP Repair]
EN "The program may respond slowly due to packing. If the console screen appears blank, press ENTER once or twice and the interface will load." 🚀 This C++ tool helps you dump and fix Enigma Protector–protected EXE files (tested from v5.x up to v7.80). It automatically dumps the main executable from memory, resets critical PE structures like IAT, OEP, relocations, and more. ⚠️ Note: As of Enigma v7.80, the dumped EXE may not run correctly due to deeper anti-dump mechanisms. The tool still extracts valid memory and headers — allowing you to continue manually. ✅ What This Tool Does: Performs multiple anti-debug checks (PEB, DebugPort, IsDebuggerPresent). Suspends other threads for stable dumping. Identifies and validates the main module in memory. Detects inline hooks to prevent faulty dumps. Dumps the full memory image of the main EXE. Rebuilds PE headers: Sets new OEP Clears relocations, TLS, and resource sections Resets checksum Finds the section where OEP resides and logs it. Performs a basic Import Address Table (IAT) rebuild. Dumps all loaded DLLs into a Dumps/ folder for further analysis. ❌ Why the Dumped EXE May Not Work (Especially in 7.x): Enigma uses dynamic unpacking, loading code in stages. Real EntryPoint (OEP) may only be valid after several layers finish. Some APIs remain encrypted or virtualized in memory, and aren’t dumped cleanly. IAT fixing is basic — no redirection or advanced import fixing is handled. .reloc, .tls, and .rsrc are cleared to avoid loader errors but may affect app logic. 🛠️ Manual Fixing Instructions: If the dumped fixed_dump.exe doesn’t run: Use a debugger like x64dbg: Run the target until all UI/windows show. Dump process memory manually from that point. Get the actual OEP from the execution trace. Use tools like: Scylla or ImpREC to rebuild IAT manually. PE-bear to fix headers or corrupt sections. Patch anti-debug or integrity checks: Most failures are due to runtime checks on dumped memory. Patch .text or .vmp sections if needed. 🔮 Future Improvements: Full IAT reconstruction with thunk redirection Delayed import and forwarded DLL fix Resource rebuild or extraction VM section cleanup (devirtualizer plugins) 📁 Output Files: File Description dump_raw.bin Raw dumped memory of EXE fixed_dump.exe PE header–repaired executable Dumps/*.dll All loaded dependent DLLs dumped 🧪 Tested On: ✅ Enigma 5.70 ✅ Enigma 6.30 ✅ Enigma 7.80 ⚠️ Enigma ⚠️ Disclaimer: This tool is meant for educational and reverse-engineering research purposes only. Use it only on software you own or have legal rights to reverse-engineer. Author is not responsible for misuse or any resulting damages. TR "Program paketleme nedeniyle yavaş yanıt verebilir. Konsol ekranı boş görünüyorsa, ENTER'a bir veya iki kez basın ve arayüz yüklenecektir." 🚀 Bu C++ Aracı ile Enigma Protector (v5.x–v7.80) Korumalı EXE Dosyalarını Dump ve Fixleyin! Bu araç, bellekte çalışan Enigma korumalı bir EXE dosyasını otomatik olarak dump'lar, PE yapısını onarır (IAT, OEP, relocations vb.) ve kullanıcının manuel analiz yapabilmesi için uygun bir hale getirir. ⚠️ Not: Enigma Protector v7.80 itibarıyla, dump edilen EXE dosyası her zaman çalışmayabilir. Bunun nedeni, daha derin anti-dump mekanizmalarının uygulanmış olmasıdır. Ancak araç hâlâ geçerli bellek ve başlık bilgilerini çıkararak manuel müdahaleye imkân tanır. ✅ Araç Ne Yapar? Birden fazla anti-debug kontrolü uygular (PEB, DebugPort, IsDebuggerPresent). Dump işlemi sırasında kararlılık için diğer thread'leri askıya alır. Ana modülü tespit eder ve doğrular. Inline hook olup olmadığını kontrol eder. EXE’nin tam bellek imajını dump’lar. PE başlıklarını yeniden yapılandırır: Gerçek OEP’i ayarlar. reloc, TLS ve resource dizinlerini temizler. Checksum sıfırlanır. OEP'in bulunduğu bölümü belirler ve bildirir. Temel seviyede IAT (Import Address Table) rebuild işlemi yapar. Yüklenmiş tüm DLL dosyalarını Dumps/ klasörüne çıkarır. ❌ Neden Dump Edilen EXE Çalışmayabilir? (Özellikle v7.x Sürümlerinde) Enigma dinamik unpacking yapar, kodu aşama aşama yükler. Gerçek EntryPoint (OEP), bazı aşamalar tamamlanmadan ortaya çıkmaz. Bellekte bazı API’ler hâlâ şifreli veya sanallaştırılmış olabilir. IAT fix işlemi temel seviyededir; yönlendirme veya gelişmiş yapılandırma yapılmaz. .reloc, .tls ve .rsrc bölümleri sıfırlandığından, uygulama mantığını bozabilir. 🛠️ Manuel Onarma Yöntemleri: Eğer fixed_dump.exe çalışmazsa: x64dbg gibi bir debugger ile hedef uygulamayı başlatın. Tüm UI (arayüz) açılana kadar çalıştırın. O noktada belleği manuel olarak dump’layın. Gerçek OEP adresini execution trace’ten tespit edin. Aşağıdaki araçları kullanarak onarma işlemlerini tamamlayın: Scylla veya ImpREC ile IAT rebuild. PE-bear ile PE başlıklarını ve bozuk bölümleri onarın. Anti-debug kontrollerini veya integrity kontrollerini patch’leyin. .text veya .vmp section’larını gerektiğinde düzenleyin. 🔮 Gelecek Geliştirmeler: Tam IAT yeniden yapılandırması (thunk yönlendirmeli) Gecikmeli import ve forwarded DLL desteği Resource rebuild veya extraction desteği VM bölümlerinin temizlenmesi (devirtualizer eklentileri ile) 📁 Oluşturulan Dosyalar: Dosya Adı Açıklama dump_raw.bin EXE’nin dump edilmiş ham belleği fixed_dump.exe PE başlığı onarılmış hali Dumps/*.dll Tüm yüklü DLL'lerin kopyaları 🧪 Test Edilen Sürümler: ✅ Enigma 5.70 ✅ Enigma 6.30 ✅ Enigma 7.80 ⚠️ Yasal Uyarı: Bu araç yalnızca eğitimsel ve tersine mühendislik araştırma amaçlıdır. Yalnızca size ait olan veya tersine mühendisliğini yapma hakkınız olan yazılımlar üzerinde kullanınız. Yazar, bu aracın kötüye kullanımından veya oluşabilecek zararlardan sorumlu değildir. link.txt
-
Themida unpacker Magicmida (3x,2x)
Supports 32-bit applications Themida automatic unpacker magicmida Restored Windows XP compatibility. Added support for Themida 1.8/early 1.9. Added support for kernelbase forwards, required by some newer games. Fixed TLS call detection in some cases. Increased Themida v3 IAT tracing limit. link.txt
-
🧠Advanced Memory Dumper 🧠💥 Dump Encrypted & Packed VMP Protected💥
💥 Dump Encrypted & Packed VMP Protected Executables Easily! 💥 🔹 Description: This is a high-performance memory dumper tool developed in C++ for advanced reverse engineers and malware analysts. The dumper can extract the full memory or individual loaded modules of a running process — even if it’s packed or protected (e.g., with VMProtect). 🧪 The tool has been tested on VMProtect-protected executables and successfully generated memory dumps of the decrypted, unpacked process in memory. 📌 Features: ✔️ Full process memory dumping (crackfrm_memory_dump.bin) ✔️ Individual module dumps with auto naming (modulename.crackfrm_dump) ✔️ Designed for packed/protected software (e.g., VMProtect) ✔️ Clean Unicode support with centered UI display ✔️ Built with full Windows API compatibility (ReadProcessMemory, VirtualQueryEx, GetModuleFileNameEx) 🧰 How It Works: 🎯 You enter the target process's PID (e.g., 8999). 📦 The tool creates: A complete binary dump of the process memory. Individual .dll and .exe module dumps from memory. 💾 Dumped files are saved to the same directory, named appropriately. 🔧 You can then fix and rebuild the dumped .exe using tools like Scylla or PE Bear. ⚠️ Why is the Dumped .exe Broken? When you dump a protected process like one packed with VMProtect: The original PE header and section structures are either modified or encrypted. What’s left in memory after unpacking is not aligned to the original file structure. Dump tools simply copy memory regions — they don’t rebuild PE headers or imports. 🛠️ How to Fix the Dump? ➡️ Use Scylla or a similar Import Reconstructor: Launch Scylla, attach to the target process before dumping. Load the dump file. Use the "IAT AutoSearch", then "Get Imports". Finally click "Fix Dump" to regenerate a usable executable. 📁 The fixed dump is saved as: dumpname.exe.bak or similar. dumperx64.exe dumperx86.exe
-
RozDll v5.53
RozDll Patcher has been upgraded to version 5.53 Change Log: 1- Added a new "HID" button in the Patcher Panel. This lets you create the Patcher without the "Run" and "Bak" buttons. It's useful if you don't want others to compare the patched file(s) with their backup(s). 2- Fixed the behavior of the "CMP" button, as reported by Mr. "Juggernaut". 3- The "ANM" Cursor Animation button is now initially disabled to allow better focus on the "Open" button. 4- Improved the design of the Icon Group Box UI. setup+portable link.txt Pass: exetools.net
-
Authix login patcher
Authix Login Patcher; Authix (https://authix.cc/) allows you to skip the login part when you inject it into any program that uses the license system. What does it support? C++ x64 supports all versions, regardless of console-IMGUI. Functions support virtualized applications. Supports packaged applications (VMProtect, Themida, etc.) link.txt
-
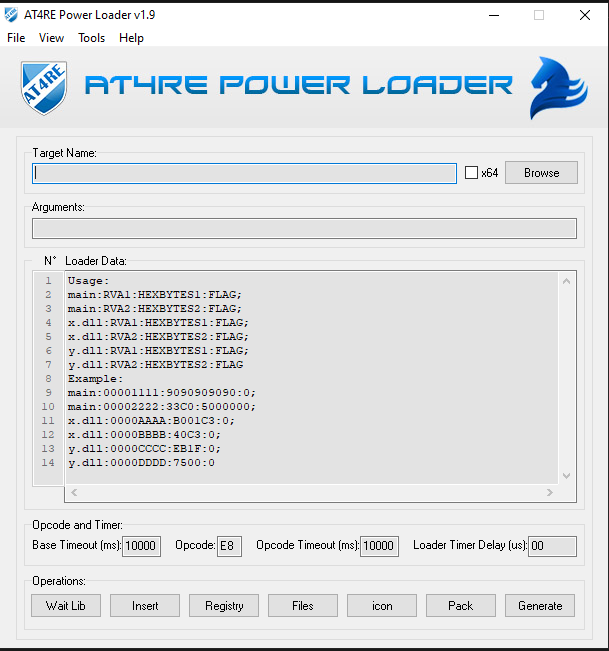
AT4RE Power Loader
====================== AT4RE Power Loader v1.50 (Release Date: 10/09/2025) ====================== v1.50 The most powerful loader against strong and complex protectors includes VM. It also works with packers, compressors, and even unprotected executable files. Main Features: [+] Fixed Environment Variables "%ProgramFiles(x86)%" to "%ProgramFiles%" in Delete Files Feature. [+] Base Timeout and Opcode Timeout Decreased to old values (5000ms) For Fast Report. [+] Fixed Bug in Import 1337 File Reported By: dragon874. Loader Details: [+] Now Loader Can Run As Admin automatically when Delete Files in "%ProgramFiles%". [+] The Loader Tested with All Features on WIN XP,7,8,10,11 (x32 & x64). Root Folder Contents: [+] Icons folder (includes 5 icons). [+] Plugin folder (AT4RE Patch Exporter.dll, How To Use.url, ReadMe.txt). [+] Project folder (Save or open projects for future use). [+] Tools Folder (includes 4 External Tools). [+] UPX folder (includes upx.exe). [+] ATPL.EXE (AT4RE Power Loader). [+] Version History.txt ================== AT4RE Power Loader v1.8 (Release Date: 07/12/2025) ================== v1.8 The most powerful loader against strong and complex protectors includes VM. It also works with packers, compressors, and even unprotected executable files. Main Features: [+] Execute Target with Specific Parameter. Feature Requested By: CodeExplorer | SND Team. Loader Details: [+] Loader Now Able to Execute any Target with any Specific Parameter. Root Folder Contents: [+] Icons folder (includes 5 icons). [+] Plugin folder (AT4REPatchExporter.dll, How To Use.url, ReadMe.txt). [+] Project folder (Save or open projects for future use). [+] Tools Folder (includes 4 External Tools). [+] UPX folder (includes upx.exe). [+] ATPL.EXE (AT4RE Power Loader). [+] Version History.txt ================== AT4RE Power Loader v1.9 (Release Date: 01/01/2026) ================== v1.9 The most powerful loader against strong and complex protectors includes VM. It also works with packers, compressors, and even unprotected executable files. Main Features: [+] Fixed Some Bugs In GUI. Loader Details: [+] Fixed Some Bugs In Loader. Root Folder Contents: [+] Icons folder (includes 5 icons). [+] Plugin folder (AT4REPatchExporter.dll, How To Use.url, ReadMe.txt). [+] Project folder (Save or open projects for future use). [+] Tools Folder (includes 4 External Tools). [+] UPX folder (includes upx.exe). [+] ATPL.EXE (AT4RE Power Loader). [+] Version History.txt AT4RE Power Loader v1.9.zip
-
AutoPatch1337 – Automatic Patch Injector for VMP, Enigma, Themida Protected EXE Files
AutoPatch1337 is an automatic patching tool developed in Visual Studio C++ designed for protected or packed Windows applications. This program launches EXE files packed with popular protection systems like VMP (VMProtect), Enigma, and Themida, then automatically applies predefined byte patches to the target memory addresses after the process is started. This way, you can quickly bypass protections or license checks without manual intervention. AutoPatch1337 performs patching securely and efficiently while showing patch details in a separate helper console application. How It Works: Patch File: AutoPatch1337 uses a text patch file named patch.1337. The first line contains the full path or name of the target EXE file. Subsequent lines specify patch offsets and the original and patched byte values. Example; >ProtectedApp.exe 1234AB:90->EB 5678CD:74->75 AutoPatch1337.exe: This program reads the patch file, starts the target application, obtains the image base address from the PEB, and writes the defined patches into the target process memory. It safely changes memory protection permissions during writing and applies patches. Patch logs are displayed in a separate process running HelperConsole.exe. HelperConsole.exe: This console application displays patch details to the user. It reads the patch file and outputs which offsets were patched and how, allowing monitoring of the patching process. How to Use: Create a patch file named patch.1337. The first line must be the full path or name of the target EXE. Write offsets and patch data in the following lines. Run MainPatcher.exe. It will load the patch file, start the target program, and automatically apply the patches. Patch details will be shown automatically in the HelperConsole.exe window. After patching, the target program will continue running; the consoles can be closed or kept open as preferred. Advantages of AutoPatch1337: Automatic Patching: Applies patches to the target EXE quickly and without manual intervention according to the patch file. Protection Bypass: Works with advanced protection systems like VMP, Enigma, and Themida by patching memory after unpacking. Patch Log: Patch details are displayed in a separate console application for verification. Safe Memory Writing: Changes memory protection and flushes instruction cache to ensure stable operation. Flexible Patch File: Offsets and bytes can be easily edited for different applications. Sample Patch File Content: >ProtectedApp.exe 1234AB:90->EB 5678CD:74->75 Conclusion AutoPatch1337 is a powerful and practical tool especially for reverse engineering and cracking purposes. It automates patching of EXE files protected or packed by advanced protection systems after launching them. This saves time, reduces errors, and simplifies the patching process. link.txt
-
Keyauth 1.3 login patcher & dumper
KeyAuth 1.3 Login-License Patcher & File Dumper This DLL file is used to skip the Login and License sections in any program you inject (Keyauth 1.3). Also, if you enter a valid license key, it dumps the file downloaded from the keyauth server and extracts it to the folder. What does it support? C++ x64 Console-IMGUI supports all versions regardless. KeyAuth or Loader functions support virtualized applications. It supports Normal or Custom-Modified KeyAuth versions. It supports packaged applications. (VMProtect, Themida etc.) link.txt
-
ExeinfoPe v.0091
The most popular scanning tool that shows what files are written with or protected with. link.txt
-
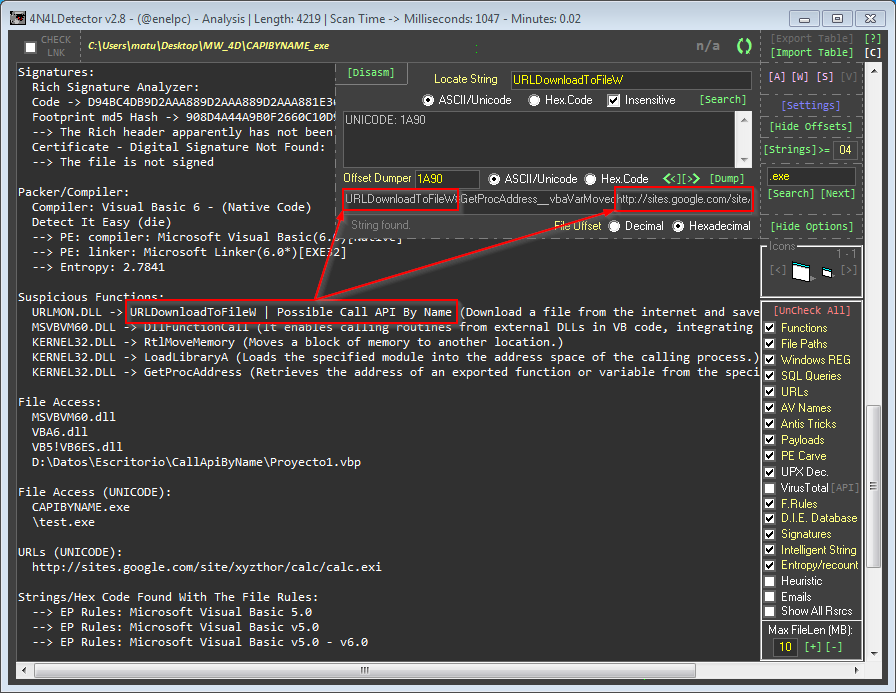
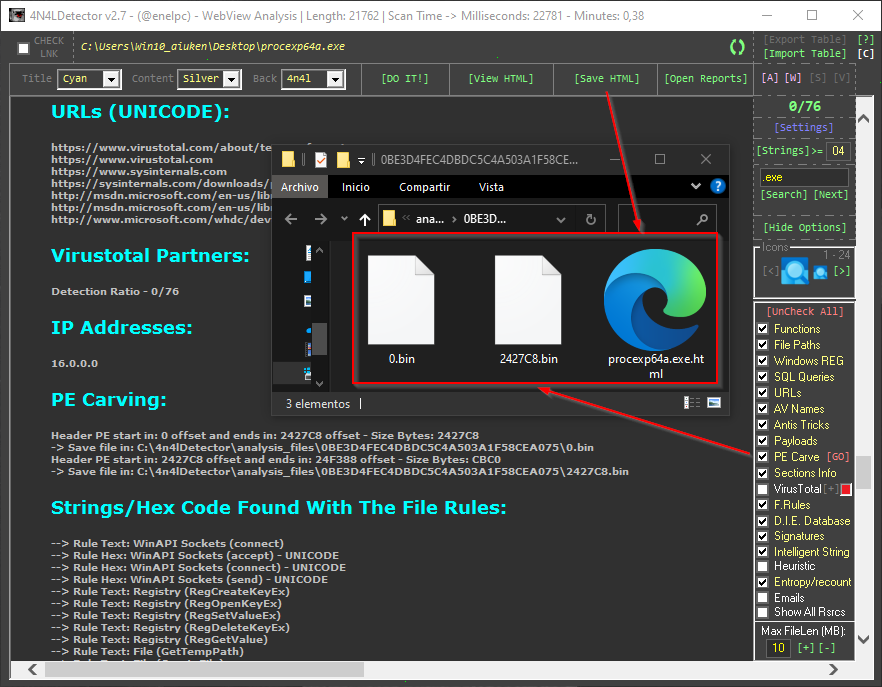
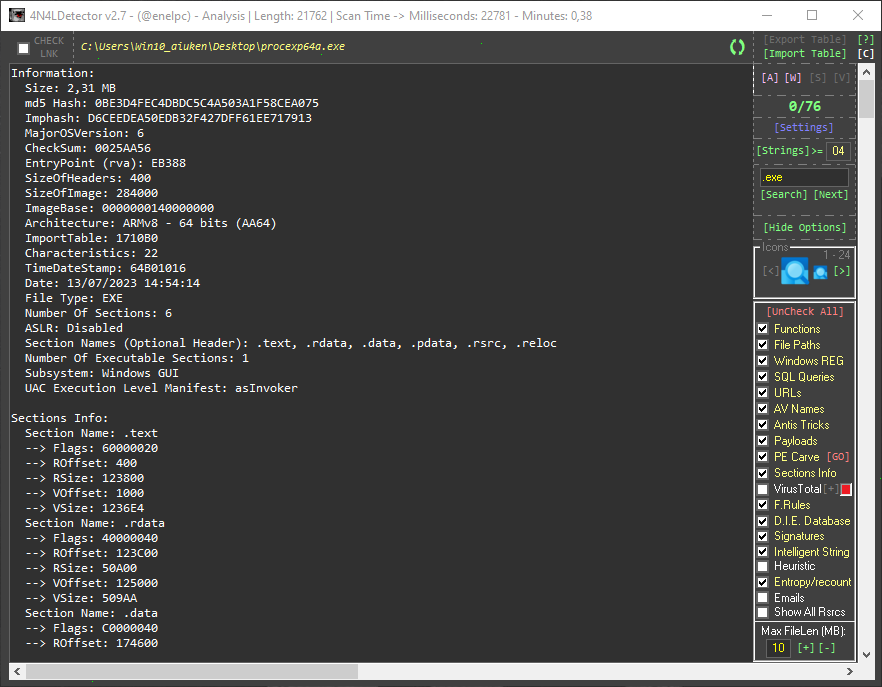
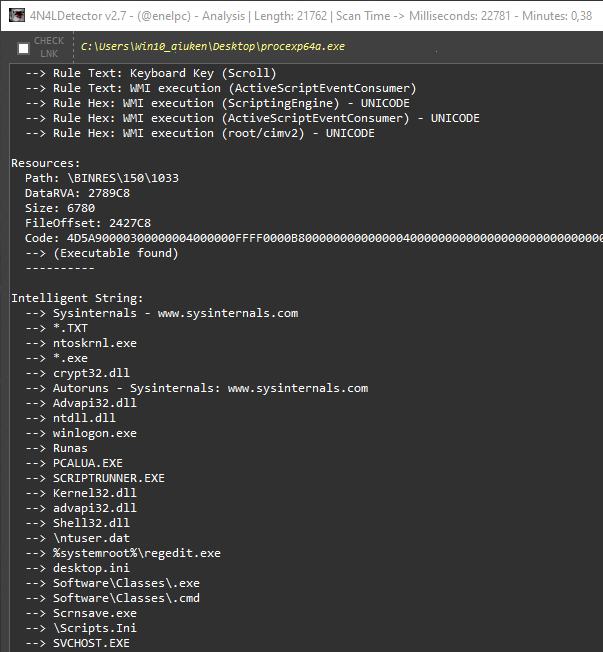
🛡️ 4n4lDetector v3.1.0 🔥 Advanced PE Scanner & Malware Analysis Tool
🚀 Exclusive Reverse Engineering & Malware Hunting Toolkit Released: 22 hours ago — Latest Version! 📝 About This Tool 4n4lDetector is a powerful and lightweight PE analysis scanner for Microsoft Windows executables, libraries, drivers, and memory dumps. Designed to make malware detection easy and intuitive, the tool provides in-depth analysis of PE header structures, sections, strings, APIs, and anomalies — giving you the upper hand in detecting modern malware techniques. It comes packed with smart heuristics, optimized detection engines, and actionable insights for reverse engineers and threat hunters. 👉 Simply drag & drop your samples — fast & intuitive! ⚡ Supported Architectures ✅ 32-bit: x86, 8086, ARMv7 ✅ 64-bit: x64, x86-64, AMD64, ARMv8 TI & ET Extraction: Alpha AXP, ARM (Thumb-2), ARM64 EFI Byte Code Hitachi SH3, SH4, SH5 Intel i860, Itanium IA-64 MIPS R3000/R4000/FPU x64, x86, x86-64 🎛️ UI Buttons Legend 🟢 Green: Action buttons (Open Files/Folders, Run Tools) 🔴 Red: Reset/Delete/Reconfigure 🟣 Purple: Online interactions 🌸 Pink: Navigation shortcuts ⌨️ Hotkeys 🔍 [A] Main Analysis 🌐 [W] HTML Report View 🔤 [S] Strings Viewer 🦠 [V] VirusTotal API Report 🧠 Detections & Features 🔎 PE Info & Structure 🛑 Unusual Entry Points & Code 📦 Packers / Crypters / Binders 🏗️ Compilations & Architectures 🧑💻 Suspicious Functions 🗝️ Registry Keys & File Access 🕵️ Anti-VM / Sandbox / Debug Detection 🌐 URL & IP Extractor 🗂️ Embedded Payloads 🛡️ AV Services Check 📄 Duplicate Sections & Rich Signature Analyzer 📬 Emails, SQL Queries, Malicious Resources 🐀 Config RAT Detection (Memory Dumps) 🧩 PE Carving & Exploit Detection 🧮 CheckSum / PE Integrity Verifications 🐍 Polymorphic Patterns 🆕 What's New in v3.1.0 🚀 ✅ Added Coronavirus Icon button redirecting to PEscan.io ✅ Full integration of Zw functions & Call API By Name detections ✅ Improved SQL info gathering (faster & more accurate) ✅ Better handling of Duplicate Sections ✅ RVA calculation adjustments for Export Table ✅ New controls for Import/Export/Resources Extraction ✅ Overflow protection & stability improvements ✅ Updated SSL compatibility for VirusTotal API ✅ Manual control for message downloads ✅ Enhanced safety for Reset & Update buttons ✅ Redesigned Report UI & HTML Reports ✅ Improved Styled HTML Extraction ✅ Optimized buffer handling & performance ✅ Added .NET version & Any CPU flag detection ✅ Centered Settings & Help windows ✅ Updated 4n4l.Rules & Entry Point rules ✅ Fixed sporadic file path errors ✅ Improved extraction of executable resources ✅ Enhanced Intelligent Strings Module (better serials & IP detection) link.txt
-
Burp Suite Professional - FULL 2025.3.2 | LOADER & KEYGEN - VIDEO TUTORIAL |
Unlock the full potential of Burp Suite Professional 2025.3.2 with this fully working Loader & Keygen! Step-by-step video tutorial is included! (Easy for everyone!) What's Included: Burp_License_Cleaner.reg BurpLoaderKeygen117.exe Burp Suite Professional 2025.3.2 Installation & Activation Video Hidden Content Installation & Activation Guide: 1. Clean Previous License Data Run Burp_License_Cleaner.reg to clean any old Burp Suite license information. 2. Generate a New License Launch BurpLoaderKeygen117.exe . In the License Text field, enter any text (your name, anything). Copy the generated License Key. Click the RUN button. Burp Suite will automatically start. 3. Apply the License Key In the Burp Suite activation window: Paste the License Key you copied. Click Next. 4. Manual Activation Choose Manual Activation option. Copy the Activation Request code shown on the screen. 5. Generate Activation Response Go back to BurpLoaderKeygen117.exe . Paste the Activation Request code into the Activation Request field. The keygen will generate an Activation Response automatically. 6. Complete Activation Copy the Activation Response. In Burp Suite: Paste it into the Paste Response field. Click Next to finish. Congratulations! Your Burp Suite Professional is now fully activated! ⚡ Video Tutorial: Watch the complete installation & activation process! link.txt Rar pass: crackfrm.com
-
HTTP Debugger 9.12 |🔧 KEYGEN - CRACK TOOL 💻|
Run the file as administrator. The process is complete, press any key to close Patcher. link.txt Rar pass: crackfrm.com
-
Steam Achievement Manager (SAM) 7.0
🎮 Take Full Control of Your Steam Achievements & Stats — Unlock, Edit, Dominate! 🚀 Steam Achievement Manager (SAM) 7.0 empowers users to unlock achievements and tweak in-game stats across any supported Steam game. With a sleek and simple interface, this tool grants access to hundreds of in-game values — and even supports batch editing across titles like CS:GO, Dota 2, and more. ✨ Key Features: 🔓 Achievement Unlocker – Instantly unlock any achievement in your favorite Steam games. 🛠️ Stats Editor – Modify in-game stats like kills, deaths, playtime, and much more. 🔄 Live Sync – Refresh or reset values directly from Steam servers. 🎮 Game List Support – Automatically detects and loads all your installed Steam games. ⚠️ Disclaimer Reminder – Alerts users that editing stats may cause unintended issues — use responsibly! link.txt
-
TelegramScraper
It can scrape and add members from one chat to another chat using some Telegram accounts. Also it can scrape hidden members of group going through group messages. Bot has very user-friendly interface. link.txt
-
🚀[NEW 1.51GB] ELITE CRACKING KITS | DUMPERS • CONFIGS • LEECHERS • TOOLS
🔥 Fresh drop for 2025 – crafted for serious crackers only. This pack includes private tools, rare configs, powerful dumpers, and custom leechers. All handpicked to boost your workflow and keep things efficient. Stay ahead of the game — quality over quantity. 🚀 Included Tools: ✨ Account Cracking Tools ✨ Bruteforcers (OpenBullet Anomaly 1.4.4 ~ OpenBullet Original ~ Sentry MBA 1.4.1 ~ Storm 2.6.0.2 ~ Woxy 3.0) ✨ Bruteforcer Configs (Openbullet Configs ~ Sentry MBA Configs ~ Storm Configs) ✨ Massive Checker Packs (Amazon Reg Checker ~ Cdkeyhouse ~ Chase Bruteforce ~ Discogs Brute ~ Golden-tea.me ~ Instagram Reg Checker ~ PayPal Software ~ Reg Checker Ebay) ✨ Premium Redeye Checkers (JustCloud ~ CoinPot ~ Deezer ~ Digital Ocean ~ Email ~ Hulu ~ Minecraft ~ Netflix ~ Spotify) ✨ Full Checker Vault (Bigstockphoto ~ Blizzard ~ Bonusbitcoin ~ CBS ~ Chegg ~ Crunchyroll ~ Directv Now ~ Grammarly ~ HBO Now ~ Lynda ~ NBA ~ Netflix Password Changer ~ NFL ~ Scribd ~ Skillshare ~ Soundcloud ~ Tidal ~ Toluna ~ Udemy ~ UFC ~ Uplay ~ WWE) ✨ Advanced Brute Checkers (NetFLix ~ NordVpn ~ Adfly ~ Adfocus ~ BruteBeast ~ BTC Clicks ~ Crunchyroll ~ Cut-URL ~ Deezer ~ FreeProxy ~ Ganna ~ Hotspot Shield VPN ~ Hotstar ~ Hungama ~ Netflix ~ Origin ~ Spotify ~ Steam ~ Successbux ~ Toluna ~ UPlay ~ WWE) ✨ Custom X-Killer Tools (Checker Wish ~ Combo Leecher ~ Combolist Generator ~ Crunchyroll Checker ~ eBay Checker ~ Freebitco.in Checker ~ Heroku Checker ~ HideMyAss! Checker ~ Hitleap Checker ~ Hotmail Checker ~ Hulu Checker ~ Instagram Checker ~ Lukiegames Checker ~ Minecraft Checker ~ Minecraftservers Checker ~ MyEarn Checker ~ Netflix Checker ~ NO-IP Checker ~ NordVpn Checker ~ Opploans Checker ~ Origin Accounts Checker ~ Ozgameshop Checker ~ Proxy Grabber ~ Pubg Checker ~ Shopfans Checker ~ Skype Checker ~ Spotify Premium Checker ~ Sunsky Checker ~ Tinydeal Checker ~ Vpsserver Checker ~ WWE Checker ~ Ytmonster Checker ~ Zenmate Checker) ✨ xPolish Checker Set (CoinPot ~ Discord ~ HMA ~ Hulu ~ Minecraft Brute ~ PlayStation Registration ~ Spotify ~ VyprVPN ~ WWE ~ Zenmate) ✨ Proxy Tools & Scrapers (Gather Proxy 9.0 Premium ~ GC Proxys ~ IP Proxy Scraper ~ Kidux Proxy Scraper ~ Net Ghost Proxy Scraper ~ ProxyScraper (Python) ~ Proxy Checker ~ Proxy Generator 1.3.6 BETA ~ Proxy Leecher ~ Proxy Scraper v1.0 ~ Proxy Shark 2016 v1.6 ~ Proxy Sources ~ Proxy Tool 1/2/3 ~ Proxy v0.3 Checker ~ Proxyscape Scraper ~ QProxyScrape ~ Sp00kyProxy ~ Unfx Proxy Checker x64 ~ Universal Proxy Software ~ μProxy) Crunchyroll Checker CyberGhost VPN Checker Express VPN Checker GearBest Accounts Checker Hide My Ass Checker HMA Accounts Checker Hulu Checker IPVanish Checker Malwarebytes Key Checker Minecraft Checker Nordvpn Checker Spotify Checker VyprVPN Checker Zenmate Acc Checker Dork Tools Duplicate Remover Hash Tool Keyword Scraper SLAYER Leecher v0.6 Split Combos SQLi Dumpers Utils And way more! link.txt
-
Cracker tools 2.9 by yildo
The installation is set up to be unattended. The file you downloaded will be named Crackers Tools 2.9 By yildo.exe. To install, just double-click and wait until a message pops up confirming the installation is complete. A 64-bit operating system is required for it to appear in the right-click menu. If it’s not showing up in the right-click menu, it means you’ve installed it on an x86 system. The Tools folder includes both x86 and x64 versions. The shortcuts you see in the image will be automatically placed on your desktop. link.txt
-
💎 Fortnite Deep Cleaner [Src Included] 💎
Fortnite Deep Cleaner Info: This is a cleaner for the fortnite game. It removes traces of hwid bans without requiring formatting. You need to spoof after the cleaner. How to Use: • Run the following command: pip install colorama • Run main script: python main.py Note: • Please note that this script makes permanent changes to Windows registry and your game installation. Use only if you accept such changes being made. link.txt
- Slotted Fortnite Cheat
-
[CRACKED] ⚡ CS2 Internal Esp + 🎯 AimBot
CS2 Internal ESP + Aim Status: Working Features AimBot Settings • AimBot • AimBot FOV • AimBot Smoothnes - Visuals Settings • Box • Name • Health • Health Text • ESP Lines • Dark Mode • Team Check link.txt
-
[CRACK] 💎 INV Only Internal CS2 Hack 🎯 Aimbot 🧠 Visuals 👾 SkinChanger ⚡ FREE! ⚡
[CRACK] 💎 INV Only Internal CS2 Hack 🎯 Aimbot 🧠 Visuals 👾 SkinChanger ⚡ FREE! ⚡ [CRACK] Invite Only Internal CS2 Hack - Aimbot - Visuals - Skin Changer Internal Assistant with auto update and real-time configuration Current Status: UNDETECTED Last Update: 13 May 2025 Features • Visuals • Chams • Aimbot • Internal • Skin Changer • Config System • Private Invite Only • Auto Update • High Performance • Illusionary.club Crack Requirements • All Resolutions Supported (Fullscreen Windowed Recommended) Installation Guide • Complete the download. Extract Extreme Injector and dll file to the same folder. • Run Extreme Injector as administrator and add the DLL. Open the game and select cs2.exe from the Process Name Select section. • Click Settings, set the Injection Method to Manual Map and save. • Start CS2 and when you come to the menu, inject by clicking the Inject button. • Menu Key: INS DOWNLOAD
-
💎 CrackFRM Internal CS2 Hack 🎯 Aimbot 🧠 Visuals ⚡ FREE! ⚡
CrackFRM Internal CS2 Hack - Aimbot - Visuals Internal Assistant with auto update and real-time configuration Current Status: UNDETECTED Last Update: 13 May 2025 Features • Visuals • Chams • Aimbot • Internal • Auto Update • High Performance Requirements • All Resolutions Supported (Fullscreen Windowed Recommended) Installation Guide • Complete the download. Extract Extreme Injector and dll file to the same folder. • Run Extreme Injector as administrator and add the DLL. Open the game and select cs2.exe from the Process Name Select section. • Click Settings, set the Injection Method to Manual Map and save. • Start CS2 and when you come to the menu, inject by clicking the Inject button. Do not close the cmd that opens. • Menu Key: END link.txt
-
💎 Valorant Assembly Simple Triggerbot [Src Included] 💎
Valorant Assembly Simple TriggerBot Info: The total reaction time of the triggerbot is about 13 ms. • Average time taken for each function: • Screen capture: 8 ms • Color detection: 0 ms • Mouse event: 5 ms How to Use: • Download the cheat. • Unzip the file and open main.exe. • Turn RawInputBuffer off in Valorant's general settings. • Set your game to Windowed Fullscreen. • Ensure enemy color matches Valorant's (Default color is purple). Developer Instructions: • Open the .sln file and build the project in x86 - Debug mode, using Visual Studio 2022 link.txt
-
💎 CrackFRM Valorant Hack 🎯 TriggerBot 🧠 Bomb Timer ⚡ FREE! ⚡
CrackFRM Valorant Hack - TriggerBot - Bomb Timer External Assistant with modern UI and real-time configuration Current Status: UNDETECTED Last Update: 10 May 2025 Features • Precision Color-based Triggerbot with dynamic FOV • Adaptive shooting patterns with randomization • Smart bomb timer with auto-defuse capability • Modern UI with real-time configuration • Profile systems for different playstyles • Stealth updates with signature spoofing Requirements • Python 3.8+ • PyQt5 • opencv-python • numpy • keyboard • mss • pywin32 • bettercam Quick Setup pip install PyQt5 opencv-python numpy keyboard mss pywin32 bettercam python main.py Configuration (config.json) { "keybind": 1, // Trigger key (e.g. LMB=1, RMB=2, etc.) "fov": 5.0, // Detection radius "shooting_rate": 65.0, // Base fire rate "min_shooting_rate": 50.0, "max_shooting_rate": 80.0, "trigger_mode": "hold", // "hold" or "toggle" "enable_press_duration": true, "press_duration_min": 0.01, // Seconds "press_duration_max": 0.05 } Common Keybinds • LMB = 1 • RMB = 2 • MMB = 4 • SIDE BUTTON #1 = 5 • SIDE BUTTON #2 = 6 • ALT = 164 • SHIFT = 160 Bomb Timer Features • Real-time plant detection • Precise countdown display • Optional auto-defuse • Customizable emergency stop (Key: Home) • Overlay positioning Pro Tips • Fine-tune FOV based on resolution • Create weapon-specific profiles • Run spoofer.py regularly • Adjust color detection for your settings • Backup your configs Installation Guide • Don't forget to download Python. • Extract the folder to the desktop and open the requirements.py file. Download the requirements. • Run the main.py file and start using it. If the menu does not appear, open the task manager and end the second python application that uses low memory. DOWNLOAD