Leaderboard
Popular Content
Showing content with the highest reputation since 12/24/2025 in all areas
-
Metin2 rb-bot pixel bot cracked
3 pointsDESTEĞİ İÇİN @GökoNullDreiNull TEŞEKKÜRLER Merhaba arkadaşlar metin2 rbbot pixel bot crack sürümü ile karşınızdayız crack'in çabuk fix yememesi adına botu herkese açık olarak paylaşmayacağım bota ulaşmanız için gerekenler aşağıda yazıyor -Vip üyeyseniz erişebilirsiniz. -Vip üyeliğiniz yok ve bota erişmek istiyorsanız 1000 tl ödeyerek bu bota sınırsız erişim sağlayabilirsiniz. -Programı aşağıdan herkes indirebilir ancak size anahtar kodu soracaktır yukarıdaki şartları sağlayan kullanıcılar programın size vereceği id numarasını bana iletirse sınırsız keyi onlara göndereceğim. İletişim; -Forumdan @cambaz adlı yöneticiye özel mesaj yada discord -Kullanım; -rb.exe yi açın discord giriş botununa tıklayın sizi discord url adresine yönlendirmek için yeni pencere açacak kapatın işiniz yok. -Tam bu esnada client üzerinde discord girişi bekleniyor yazar o sırada pompaa.exe yi açın. -Client sizi başarılı bir şekilde key ekranına yönlendirir, key kısmına bir şeyler sallayıp girin hepsi bu kadar. -rb.exe çalıştıkça pompaa.exe nin açık kalması iyi olur. -Uygulama üzerinden tekrar çıkış yapmadıkça discord ekranı tekrar gelmez ancak keyin başarılı olması için pompaa.exe yi çalıştırmanız gerekir. -pompaa.exe den çıkış yapmadan önce lütfen console ekranında enter tuşuna basın ve temizliğin yapılmasını bekleyin. -İyi oyunlar. DOWNLOAD.txt3 points
-
🎁 New Year Special: Some of our Members Promoted to Full Member
📝 Topic ContentHello everyone, As a New Year special, we have applied a one-time promotion for our active community members. As part of this promotion, active normal members of the forum have been moved to the Full Member group based on the following criteria: Registered on the forum for at least 120 days Visited the forum within the last 15 days Still in the Member (normal user) group Members who met these conditions were automatically promoted to Full Member. 🎊 Promoted MembersThe following members have been promoted during this New Year special: @Han Tae Sul @Byvicci @Thrysis @0x22 @Nisrja @hern0s @Tenden @rose02 @mondschein @nhansinh @opratot @telegrambackup7 @killua7455 @meteorapollo @softwarecrackguru @Kamlesh @alisafei @pofonya @NickBounce0x3 @daiklap 🎉 Congratulations to all promoted members! ℹ️ Important NoteThis promotion was New Year–only and applied once There is no active group promotion running at the moment Full Member status will not be reverted Being active and contributing to the forum is always appreciated and may be rewarded again in the future 😉 We wish everyone a Happy New Year and a great year ahead! 🥂3 points
-
🧠Advanced Memory Dumper 🧠💥 Dump Encrypted & Packed VMP Protected💥
💥 Dump Encrypted & Packed VMP Protected Executables Easily! 💥 🔹 Description: This is a high-performance memory dumper tool developed in C++ for advanced reverse engineers and malware analysts. The dumper can extract the full memory or individual loaded modules of a running process — even if it’s packed or protected (e.g., with VMProtect). 🧪 The tool has been tested on VMProtect-protected executables and successfully generated memory dumps of the decrypted, unpacked process in memory. 📌 Features: ✔️ Full process memory dumping (crackfrm_memory_dump.bin) ✔️ Individual module dumps with auto naming (modulename.crackfrm_dump) ✔️ Designed for packed/protected software (e.g., VMProtect) ✔️ Clean Unicode support with centered UI display ✔️ Built with full Windows API compatibility (ReadProcessMemory, VirtualQueryEx, GetModuleFileNameEx) 🧰 How It Works: 🎯 You enter the target process's PID (e.g., 8999). 📦 The tool creates: A complete binary dump of the process memory. Individual .dll and .exe module dumps from memory. 💾 Dumped files are saved to the same directory, named appropriately. 🔧 You can then fix and rebuild the dumped .exe using tools like Scylla or PE Bear. ⚠️ Why is the Dumped .exe Broken? When you dump a protected process like one packed with VMProtect: The original PE header and section structures are either modified or encrypted. What’s left in memory after unpacking is not aligned to the original file structure. Dump tools simply copy memory regions — they don’t rebuild PE headers or imports. 🛠️ How to Fix the Dump? ➡️ Use Scylla or a similar Import Reconstructor: Launch Scylla, attach to the target process before dumping. Load the dump file. Use the "IAT AutoSearch", then "Get Imports". Finally click "Fix Dump" to regenerate a usable executable. 📁 The fixed dump is saved as: dumpname.exe.bak or similar. dumperx64.exe dumperx86.exe2 points
-
Metin2 CulMaster Hack Crack - Farmbot,Captcha Solver ve daha fazlası
-Zaman harcamaya değecek bir program değil istek geldi diye baktık full member üyeler indirebilir key falan yoktur. -Gelen hata mesajlarına devam diyerek programı kullanmaya devam edin yaptığı şifrelemeden attirubute çağrılarından dolayı kaynaklanır önemi yoktur. -Programı kullanmadan önce aşağıdaki program bilgisayarınızda kurulu olsun. Visual C++ Redistributable Runtimes All-in-One AIO RUNTIMES Hile ek dosyası aşağıdadır. DOWNLOAD.txt2 points
-
Rubinum capture protection bypass
2 pointsson sürüm için güncellendi aşağıdan indirin rubipatcherv1.2.txt2 points
-
DELEAKER 2025.16 CRACKED
2 pointsDeLeaker 2025.16 (Profiler for C++, C#, .NET and Delphi) C++ memory leak detection Deleaker is an extension for all major IDEs and a standalone application for memory leak detection - memory, GDI, and handles so far. Even the most stable of Windows applications are not immune to resource leaks. And of all the bugs and issues, memory leak detection tends to be the most difficult, especially when found in GDI objects and menus. And the golden rule of thumb is that the sooner bugs are found and dealt with, the less expensive they prove to be. While there's no shortage of tools and add-ons to help track down memory leaks, few are capable of tracking GDI resource leaks that can devastate Windows performance. Deleaker is one of the few tools capable of this, and will have a minimal impact on your application's performance. Deleaker is a memory leak detector that integrates with all major IDEs: Visual Studio, Delphi, C++ Builder, and Qt Creator. Homepage Link DeLeaker.txt2 points
-
Primordial CS2 Cracked By LOLSHAN
Crack Date ~ 22.07.2025 Cracked By ~ LOLSHAN Cheat Base/Source ~ Own Protectors ~ VMP [UnPacked] : License Checks [Patched] : Hooks [Manually loaded] link.txt / Virustotal Kullanım: Video 1-) Oyunu açıp Dll'i inject edin (ManualMap). Bu kadar. (ExtremeInjector Github) Daha fazla Bilgi: VMP VM'lerine çok güvenmişsin be krşm 😄 Server Mapper'i çok kötü adresler açık. Auth'da kötü ve WolfSSL kullanıyor (Hooklayıp socket'den aldığı static hile verilerinin packet'lerini verdim) VEH ile lisans kontrolünde hw-bp kullanıp register spoof ve runtime'da (rcx, rbp) atamalar yapıyor. (Manuel hallettim) Hilenin kullandığı hookları üşendiğim için manuel mapledim (Import'larda manuel). Bunlara ek olarak Dump->VMP Unpack + Patchler haricinde Cracklemek için başka bir şeye gerek yok ^-^1 point
-
Advanced Anti-Debug + Fake Entry + TLS Callback (Source Code C++)
IMPORTANT NOTE: IT IS NECESSARY TO REMEMBER THAT THERE IS NO RUNTIME PATCH OR STRING OBF IN THE PROJECT. THAT IS WHY YOUR STRINGS WILL BE READ IN PAUSE MODE EVEN IF THE PROGRAM IS NOT START FROM DEBUGGER BECAUSE IT DOES NOT HIDE PE SECTIONS. IT IS RECOMMENDED TO USE THIS PROJECT WITH VMP ENGIMA OR CODE VIRTUALIZER. EN What Is This Project? This project provides an advanced Anti-Debugging system for Windows applications. The code combines multiple techniques with TLS Callback and Fake EntryPoint, ensuring that the application can terminate itself (TerminateProcess) even before reaching the real program entry. 🔹 Techniques Used IsDebuggerPresent / CheckRemoteDebuggerPresent → Standard API checks PEB (Process Environment Block) Flag → BeingDebugged detection NtQueryInformationProcess → Low-level debug port check Inline Hook Detection (ntdll.dll) → Detects ScyllaHide / TitanHide patches Debugger Window Scan → Searches for x32dbg, x64dbg, OllyDbg window names Timing Attack → Uses QueryPerformanceCounter to detect delays Debug Register (DRx) Check → Hardware breakpoints detection TLS Callback → Runs before the program’s main entry point Fake EntryPoint → Hides the real entry, runs anti-debug first 🔹 Defense Against ScyllaHide & TitanHide Tools like ScyllaHide / TitanHide patch APIs to hide the debugger. This code counters them by: Inline hook detection → finds their patches. Timing checks → detects manipulation of execution speed. Debug registers scan → uncovers HW breakpoints. 👉 Result: Even with ScyllaHide/TitanHide, the app will terminate immediately. 🔹 Is It Enough Alone? Not fully. This provides a strong baseline but cannot guarantee 100% protection. Skilled reverse engineers may bypass it. Therefore, the best approach is to combine with VMProtect, Themida, or other virtualization tools. Recommendation: You don’t need to enable VMProtect’s anti-debug features (this code already covers them). Instead, enable virtualization, mutation, and control flow obfuscation. This way, strings, logic, and sensitive routines remain hidden. Installation instruction: In Project Properties > Linker > Advanced > Entry Point set it to FakeEntry ÖNEMLİ NOT : UNUTMAMAK GEREKLİDİR Kİ PROJEDE HERHANGİ BİR RUNTİME PATCH VEYA STRİNG OBF BULUNMAMAKTADIR BU YÜZDEN PROGRAM DEBUGGER ÜZERİNDEN START OLMASA BİLE PE SECTIONLARI GİZLEMEDİĞİ İÇİN PAUSE MODDAYKENDE STRİNGLERİNİZ OKUNACAKTIR BU PROJEYİ VMP ENGİMA VEYA CODE VİRTUALİZER İLE BİRLİKTE KULLANMANIZ ÖNERİLİR TR Bu Proje Nedir? Paylaştığım proje, Windows tabanlı uygulamalar için gelişmiş Anti-Debug sistemi içeriyor. Kodlar, klasik yöntemlerin yanında TLS Callback ve Fake EntryPoint mekanizmaları ile çalışıyor. Böylece uygulama, daha main() veya WinMain() fonksiyonuna bile ulaşmadan debug edildiğini fark ederse kendini sonlandırıyor (TerminateProcess). 🔹 Kullanılan Teknikler IsDebuggerPresent / CheckRemoteDebuggerPresent → Standart API tespitleri PEB (Process Environment Block) Kontrolü → BeingDebugged flag NtQueryInformationProcess → Kernel seviyesine yakın debug port kontrolü Inline Hook Kontrolü (ntdll.dll) → ScyllaHide / TitanHide patch’lerini tespit edebilir Debugger Window Scan → x32dbg, x64dbg, OllyDbg gibi pencere isimlerini arar Timing Attack → QueryPerformanceCounter ile sleep manipülasyonlarını yakalar Debug Register (DRx) Kontrolü → HW breakpoint’leri algılar TLS Callback → Programın EntryPoint’ine girmeden önce anti-debug çalışır Fake EntryPoint → Gerçek giriş gizlenir, önce kontrol yapılır 🔹 ScyllaHide & TitanHide Karşısındaki Gücü ScyllaHide / TitanHide gibi araçlar, IsDebuggerPresent, NtQueryInformationProcess gibi standart API’leri hook’layarak debugger’ı gizler. Ancak bu kod: Inline Hook tespiti yaparak, bu araçların yaptığı patch’leri algılar. Timing saldırısı sayesinde debugger’ın yavaşlatma girişimlerini fark eder. Debug Register taraması ile HW breakpoint’leri ortaya çıkarır. Sonuç: ScyllaHide veya TitanHide kullanılsa bile uygulama, büyük ihtimalle terminate olur. 🔹 Tek Başına Yeterli mi? Hayır. Bu kod güçlü bir temel sağlar ama tek başına %100 koruma değildir. Profesyonel reverse engineer’lar bu katmanı aşabilir. Bu nedenle, kodu VMProtect, Themida veya farklı bir Virtualizer ile birleştirmek gerekir. Önerim: VMProtect’in kendi anti-debug sistemini açmanıza gerek yok (çünkü bu kod zaten fazlasını yapıyor). Yalnızca Virtualization / Mutation / Control Flow Flattening gibi diğer koruma özelliklerini açın. Böylece stringler, kod blokları ve logic tamamen gizlenir. Kurulum Talimatı: Project Properties > Linker > Advanced > Entry Point kısmına FakeEntry yaz For those who want to test, try sending a sample crack me patch. VMP's anti-debug protection is disabled, the project uses its own protection. Test etmek isteyenler için örnek bir crack me patch atmayı deneyin vmp nin anti debug koruması kapalı projenin kendi korumasını kullanıyor link.txt1 point
-
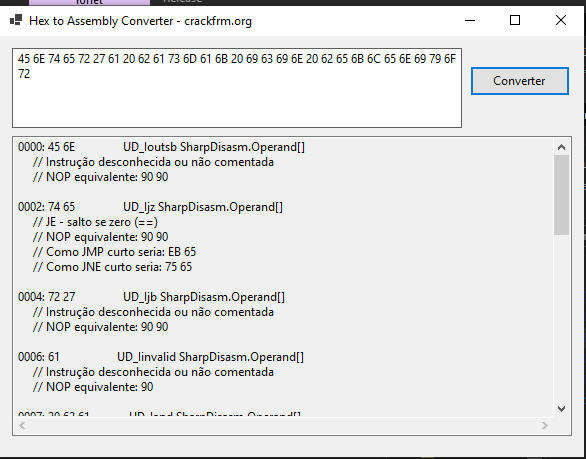
[Source Code] HexToAsm Converter
1 pointThis program is written in C# using SharpDisAsm. It converts hexadecimal code to assembly code and provides brief information. It requires .NET 6.0. HexToAsmConverter.rar1 point
-
metin2 bear - lycanshield anti cheat full bypass
çiçeğim lycan nerelerdesin ? konuyu görüyorsan satın al bi bak bakalım olmuş mu xd eline sağlık cambazz1 point
-
metin2 bear - lycanshield anti cheat full bypass
1 point
-
Themida 3.2.4.52 x32-x64 (Licensed)
1 point
-
🛠️ Complete .NET VMProtect Unpacking Toolkit + Step-by-Step Tutorial (v3.5 and Below)
👋 Hello dear CrackFrm members, 🔓 Today, I'm sharing unpack tools, a sample UnpackMe, and a detailed tutorial for VMProtect up to version 3.5 .NET. 📹 By watching the video, you can experiment with the included UnpackMe file and later test your skills on other applications as well. ⚙️ Note: These tools are designed for .NET-based applications and won't work on native ones. 💬 Happy reversing and enjoy the forum! 🛠️ Crack Tools Included: 🧭 CFF Explorer – Inspect and edit PE headers with ease 🛡️ ConfuserEx.Resource.Fixer – Fix messed up resources from ConfuserEx 🧬 VMP Demutation – Undo VMProtect .NET mutation layers 🧹 RemoveAndFixCCTOR – Clean up and fix static constructors ⚔️ VMP.NET-KILL v2.1 – Targeted tool to kill VMProtect for .NET 🚫 VMProtectNoDelegates – Bypass VMProtect delegate obfuscation 🧰 VMUnprotect.Dumper – Dump protected assemblies for analysis 🎯 Extra Challenge: 🧪 vmprotect_challenge_me.exe – A special UnpackMe file to test your skills! link.txt1 point
-
PURE LOGS RECOVERY v4 | GUI | BRUTE FORCE EXTENSION WALLET
Password:26 MEGA 4shared Box Mediafire Brute-force MetaMask extension Exodus extension Trust extension Phantom extension BraveWallet Exodus Dekstop1 point
-
Obsidium_v1.5.2_x86__Build_11 - FULL
Obsidium_v1.5.2_x86__Build_11 - FULL [*] Extract the ZIP File. Follow the instructions in the Obsidium_License.txt file and activate the license. link.txt RAR PASS : crackfrm.com1 point
-
CYBER TRIAGE 3.16.0 PWN3RZS
1 pointCyber Triage is automated DFIR software that empowers your team to quickly investigate incidents. Scores artifacts so you quickly focus on relevant data. Scans executables with 40+ malware detection engines. Recommends artifacts so you follow up on all leads. Integrates with EDRs for rapid endpoint triage after alerts. Deploys in environments agents can’t be used. Collects evidence even when EDR evasion is used. Coming soon: Hybrid AI with agentic AI + deterministic scoring. Home page Cyber tri.txt1 point
-
Microsoft Edge Remover
1 pointIntroduction Microsoft Edge Remover is a tool designed to help Windows users remove Microsoft Edge Chromium and Edge UWP from their devices. System Requirements The Microsoft Edge Remover tool requires a Windows operating system to function. It is compatible with Windows 10 (all versions) and Windows 11. Before using the tool, it is important to ensure that the user's device meets the system requirements. This will ensure that the tool runs smoothly and effectively removes Microsoft Edge Chromium and Edge UWP. The tool may also require administrator permission to run, depending on the user's version of Windows. By having the correct system requirements, users can be confident that the Microsoft Edge Remover tool will work efficiently on their device. link.txt1 point
-
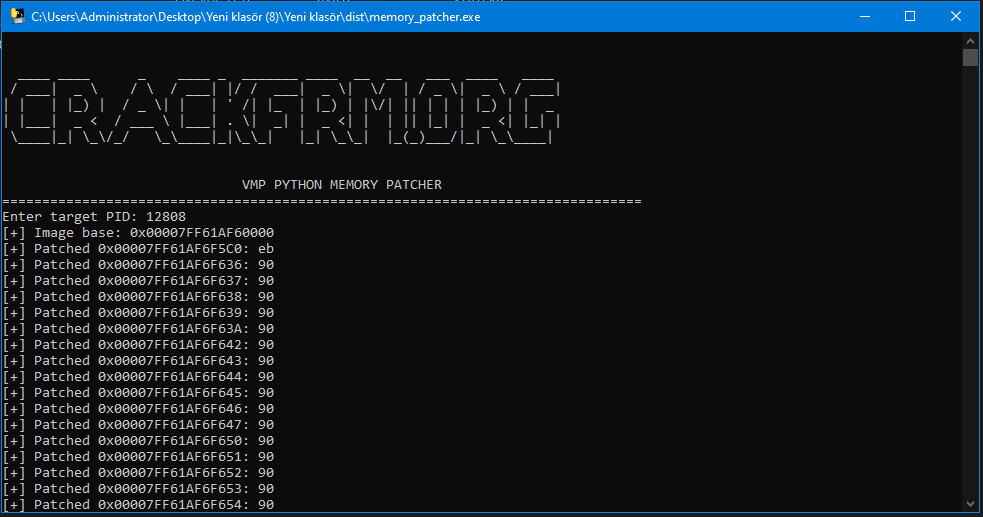
[SOURCE CODE] VMProtect Python Memory Patcher
What Does This Code Do? This Python code bypasses protection mechanisms of VMProtect (VMP) protected software by making runtime modifications in memory. The code directly writes to the target process's memory space, changing bytes at predetermined memory addresses. How It Works? THIS PROGRAM ALLOWS YOU TO PERFORM PATCH PROCESS WITHOUT NEEDING THE .1337 FILE Open the .py file with notepad and replace the sample patch addresses with the patch addresses you made in your target application. Process Access: Obtains the target process's PID and gains access with read and write permissions. Image Base Detection: Finds the base address where the process's main module (usually the .exe file) is loaded in memory. Memory Protection Change: Alters the protection levels of target memory regions to make them writable. Byte Patching: Changes bytes at predefined offset addresses with new values. Protection Restoration: Restores the original protection levels of the modified memory regions. link.txt1 point
-
HTTP Debugger 9.12 |🔧 KEYGEN - CRACK TOOL 💻|
Run the file as administrator. The process is complete, press any key to close Patcher. link.txt Rar pass: crackfrm.com1 point
-
Themida/Winlicense unpacker (Unlicense)
Themida 3.x - 2x unpacker ımport fixer unlincense 32&64 bit A Python 3 tool to dynamically unpack executables protected with Themida/WinLicense 2.x and 3.x. Warning: This tool will execute the target executable. Make sure to use this tool in a VM if you're unsure about what the target executable does. Note: You need to use a 32-bit Python interpreter to dump 32-bit executables. Feautures; Handles Themida/Winlicense 2.x and 3.x Handles 32-bit and 64-bit PEs (EXEs and DLLs) Handles 32-bit and 64-bit .NET assemblies (EXEs only) Recovers the original entry point (OEP) automatically Recovers the (obfuscated) import table automatically link.txt1 point
-
VMP VMProtect Ultimate 3.9.4 Build 2355
Different crack and done very recently Spoiler link.txt Password: @DotNetLab1 point
-
Keyauth Patcher (.NET)
1 pointIf there is protection in the .exe, unpack it first, otherwise it will not work On request, keyauth .net patcher is available for you to use with drag and drop or file location. link.txt1 point
-
Undetected Modded VMware (Bypass all anti-cheat systems.)
- 21 downloads
- Version 1.0
RAR PASS: crackfrm.org I'm happy to share this important file with you. -This is a modified VMware, not one of those silly mods; everything has been changed. -This VMware was being sold at high prices by a Chinese forum through a licensing system, but we're bypassing that and offering it to you. -Thanks to the prominent figure in the Metin2 industry for their support :) How to use it and where has it been tested? -It has been tested everywhere except Valorant and works successfully. Rascal Anticheat recently announced a fix, but it might be possible to bypass it through manipulation. For Valorant, there are people who have tested it and will let us know; we haven't tested it ourselves. -As seen in the screenshot, the modified VMware files are VMware's own installation files. If you don't know how to use them and this is your first time using VMware, ask CheatGPT; it might help :) -When you open the virtual PC, you'll find 3 spoofers on the desktop. Every time you open VMware, you can use it undetected by running the file named spoof1. Have a good time on the forums everyone!1 point -
FracQ [GF] | Farm Bot & Range Damage
StreamableWatch fracq | Streamable PROGRAMIN SAĞ ÜSTÜNDE BULUNAN + BUTONUNA BASARAK METİN2 CLİENTİNİ SEÇİNİZ ARDINDAN PROGRAM ÜSTÜNDE SOL KISIMDA KULLANICI ADINIZI GÖREBİLİRSİNİZ VE PROGRAMI KULLANABİLİRSİNİZ. Özellikler Farm Bot (Normal - Rota) Damage (Normal - Exploit - Safe) Harita Üstünden Teleport Seçilen Mape Teleport Haraket Hızı Render (Cpu - Gpu boost) Oto Pot ( Kırmızı - Mavi) Revive Wait Hp Pickup Sell (İtem Satma) Ayar - Rota Kaydetme Map resimlerinin görünmesi ve programın düzgün çalışması SimhiGF Klasörünü C diskinizin içine atınız Download.txt1 point
-
Metin2 CulMaster Hack Crack - Farmbot,Captcha Solver ve daha fazlası
Pyinstaller koruması dandik zaten.1 point
-
Metin2 CulMaster Hack Crack - Farmbot,Captcha Solver ve daha fazlası
dünyanın en kötü hilesi valla billa eline sağlık1 point
-
IDA PRO V9.3.251224 BETA1 ALL O/S
1 point
-
Windows 10 boot loader source code
This is not my work, but it’s not freely available either To review this you will need something like visual studio win10boot src code.txt1 point
-
Themida/Winlicense unpacker (Unlicense)
1 point
-
Metin2 Mobware v4 Crack Yardım
1 pointMobware v4 arkadaşlar ücretlidir TR için Kullanıcı la, e-mail, key Soran ekranı var Mobware v4 ucretli Virüs Total1 point
-
De4dot for (DNGuard v3.6 - 3.9) (Build)
1 point
-
Xerin + Source code
1 point
-
UPX 5.0.2 x32_x64
1 point
-
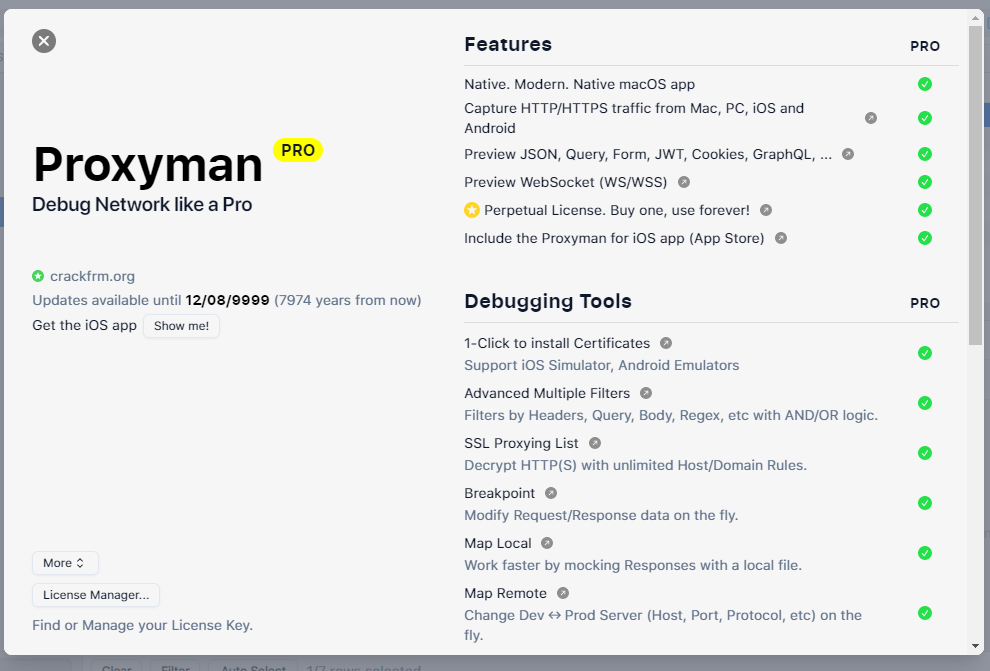
[CRACK] Proxyman PRO v2.19.0
1 pointCapture HTTP(s) in a few clicks. Best-in-class native Windows app to capture, decrypt, and mock your HTTP(s) requests/ responses with powerful debugging tools. Interventions made: Licensed until 12/08/9999. License manipulated for use on unlimited devices. Updates are completely disabled. Fixed an issue where the program would reset the license on every startup. How to use: -Replace the given crack file with the file in the resources folder in the program's file location. -If it gives a new update warning, do not accept it. -Go to the proxyman menu from the top left menu, now go to the license section and enter a license key. That section will fill itself automatically. If not, enter this license key: PXM-MET-CRACKFRM. That's all. RAR PASS: crackfrm.org link.txt1 point
-
AutoPatch1337 – Automatic Patch Injector for VMP, Enigma, Themida Protected EXE Files
Powerful !1 point
-
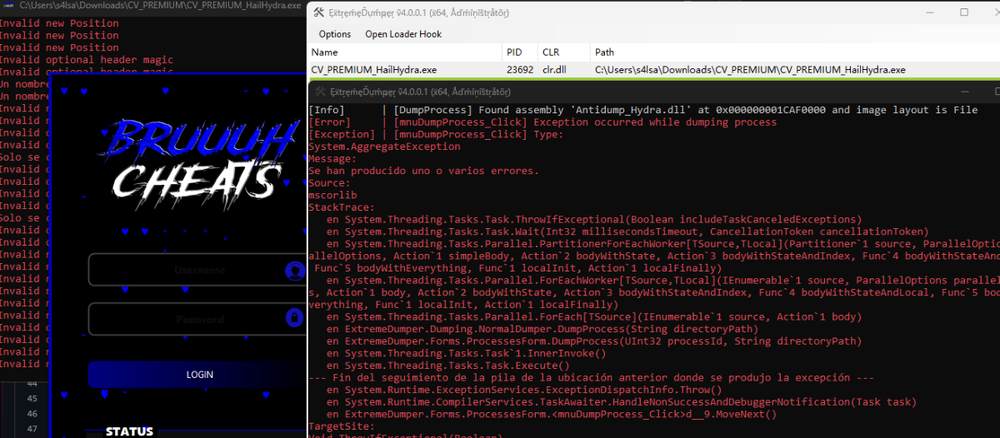
[SOURCE CODE] C# Extreme AntiDump
1 point
-
🎁 New Year Special: Some of our Members Promoted to Full Member
Congratulations to all the above members keep up the good work.1 point
-
Burp Suite Professional - FULL 2025.3.2 | LOADER & KEYGEN - VIDEO TUTORIAL |
Unlock the full potential of Burp Suite Professional 2025.3.2 with this fully working Loader & Keygen! Step-by-step video tutorial is included! (Easy for everyone!) What's Included: Burp_License_Cleaner.reg BurpLoaderKeygen117.exe Burp Suite Professional 2025.3.2 Installation & Activation Video Hidden Content Installation & Activation Guide: 1. Clean Previous License Data Run Burp_License_Cleaner.reg to clean any old Burp Suite license information. 2. Generate a New License Launch BurpLoaderKeygen117.exe . In the License Text field, enter any text (your name, anything). Copy the generated License Key. Click the RUN button. Burp Suite will automatically start. 3. Apply the License Key In the Burp Suite activation window: Paste the License Key you copied. Click Next. 4. Manual Activation Choose Manual Activation option. Copy the Activation Request code shown on the screen. 5. Generate Activation Response Go back to BurpLoaderKeygen117.exe . Paste the Activation Request code into the Activation Request field. The keygen will generate an Activation Response automatically. 6. Complete Activation Copy the Activation Response. In Burp Suite: Paste it into the Paste Response field. Click Next to finish. Congratulations! Your Burp Suite Professional is now fully activated! ⚡ Video Tutorial: Watch the complete installation & activation process! link.txt Rar pass: crackfrm.com1 point
-
Malwarebytes Full + Patcher
1 pointMalwarebytes 5.1.2.9 full version + patcher How to use; 1. Run the patch and wait for the status in the console. 2. In the console when you see the status "waiting install Malwarebytes..." --> run MBSetup.exe and install Malwarebytes. 3. After installing Malwarebytes, in the console you will see the status "waiting exit Malwarebytes..." --> close Malwarebytes in the tray, after which you will see the message "Enjoy Premium". 4. Enjoy :) IMPORTANT:; if Malwarebytes was previously installed --> UNINSTALL and RESTART your computer, otherwise the patch will not work. Also recommended disable Windows Defender for the patch to work correctly. Sometimes a message pops up "Unable to contact license server..." - this is due to the fact that the license server is specifically blocked in the hosts so that the license does not reset. Don't worry, the license still works. Just close the message box and try not to update Malwarebytes. P.S. if you fail to get premium, just try again (sometimes it takes 3 tries), but before running the patch, be sure to uninstall Malwarebytes and restart your computer. link.txt1 point
-
IDA Pro v9.2 Final
1 pointTHIS IS NOT BETA, IT IS THE LAST VERSION MAC+LINUX+WINDOWS PORTABLE link.txt LİNK UPDATED (11.11.2025)1 point
-
DELEAKER 2025.16 CRACKED
1 point
-
Resident Evil 4 HD ( Steam ) Trainer Freeze Enemys
1 point
-
[MODDED] Undetected x64dbg & x32dbg
- 24 downloads
Known and popular blocking points for x64dbg and x32dbg have been modified. It is compiled from source code and presented to you from scratch, along with popularly used plugins. titanhide scylla hide scylla bymax tools hyper hide1 point -
Themida/Winlicense unpacker (Unlicense)
1 point
-
Ida pro 9.2.250730 Beta 2 Windows only
Python script Put the script into program directory and run the script with python1 point
-
Burp Suite Professional İndir – Full v2025.7.3
Download Burp Suite Professional – Full v2025.7.3 With Burp Suite Professional, you can test your web applications for security and determine whether they pose a risk. This highly useful program can be run in your browser, configured, and easily analyzed. Burp Suite Professional's advanced features allow you to identify which applications pose a risk to your computer, identify potential slowdowns, and determine how much they slow down your computer. Its simple and user-friendly interface allows you to implement these features effortlessly and seamlessly, allowing you to gradually gain control of the program. RAR PASS: 12345 link.txt1 point
-
🔧 C++ Enigma Protector 5.x–7.x Dumper & PE Fixer Tool [Dump + Auto IAT + EP Repair]
1 point




.png.6853eaf0f6da03aa3fe5b1c6bd5167a4.png)